At Vector Flow, we are constantly working behind the scenes to innovate new product improvements and solutions that make things easier for you – easier to detect threats, easier to manage your security teams, and easier to understand your access control data. Our ultimate goal is to eliminate your manual security tasks by introducing physical security automation tools that allow you to save time and reduce security spend.
That is why we are proud to announce a series of significant product updates for Q4 that are set to revolutionize the way you manage security risks and operational tasks.
Insider Threats App: Updated Dashboard & Incident Reporting for Fast Insider Risk Identification
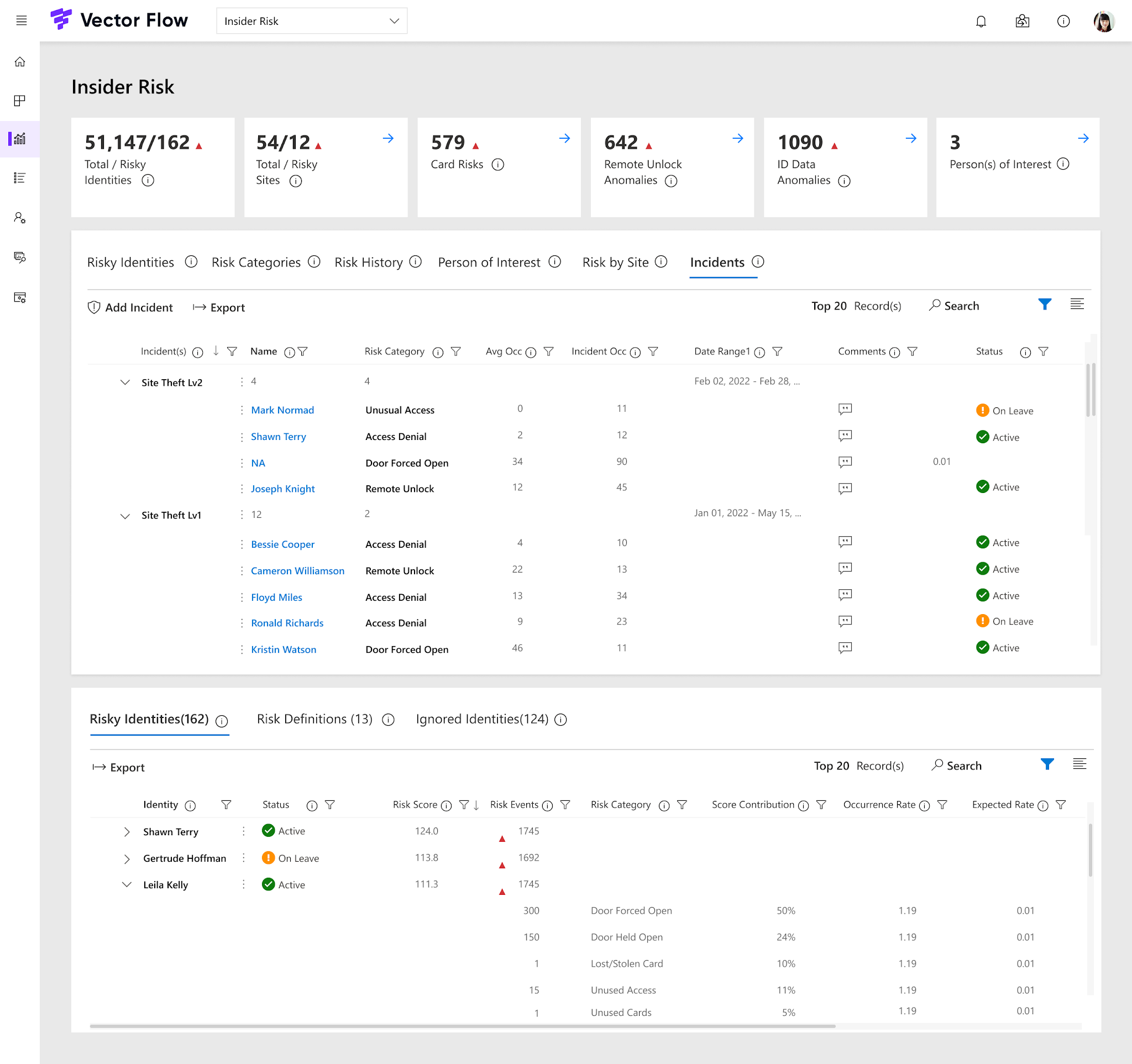
Regardless of the industry you operate in, staying ahead of potential risks is not just a priority; it’s a necessity. Utilizing new risk scoring mechanisms, the updated Insider Threats App prioritizes threats effectively, allowing you to not only detect but also respond to insider threats in real time.
Functions
- Provides real-time threat monitoring and alerts, mitigating potential damage
- Risk-scoring mechanisms prioritize threats for clear visibility and strategic resource allocation
Business Impact
- Fast incident alerts empower operators to view all physical security anomalies in real time
- Reduces both investigation duration and manual workload substantially
- Provides a strategic response with data-driven forensic practices
Intelligent Badging: Introducing ‘Use it or Lose it’ Badge Auditing Tool for Proactive Security
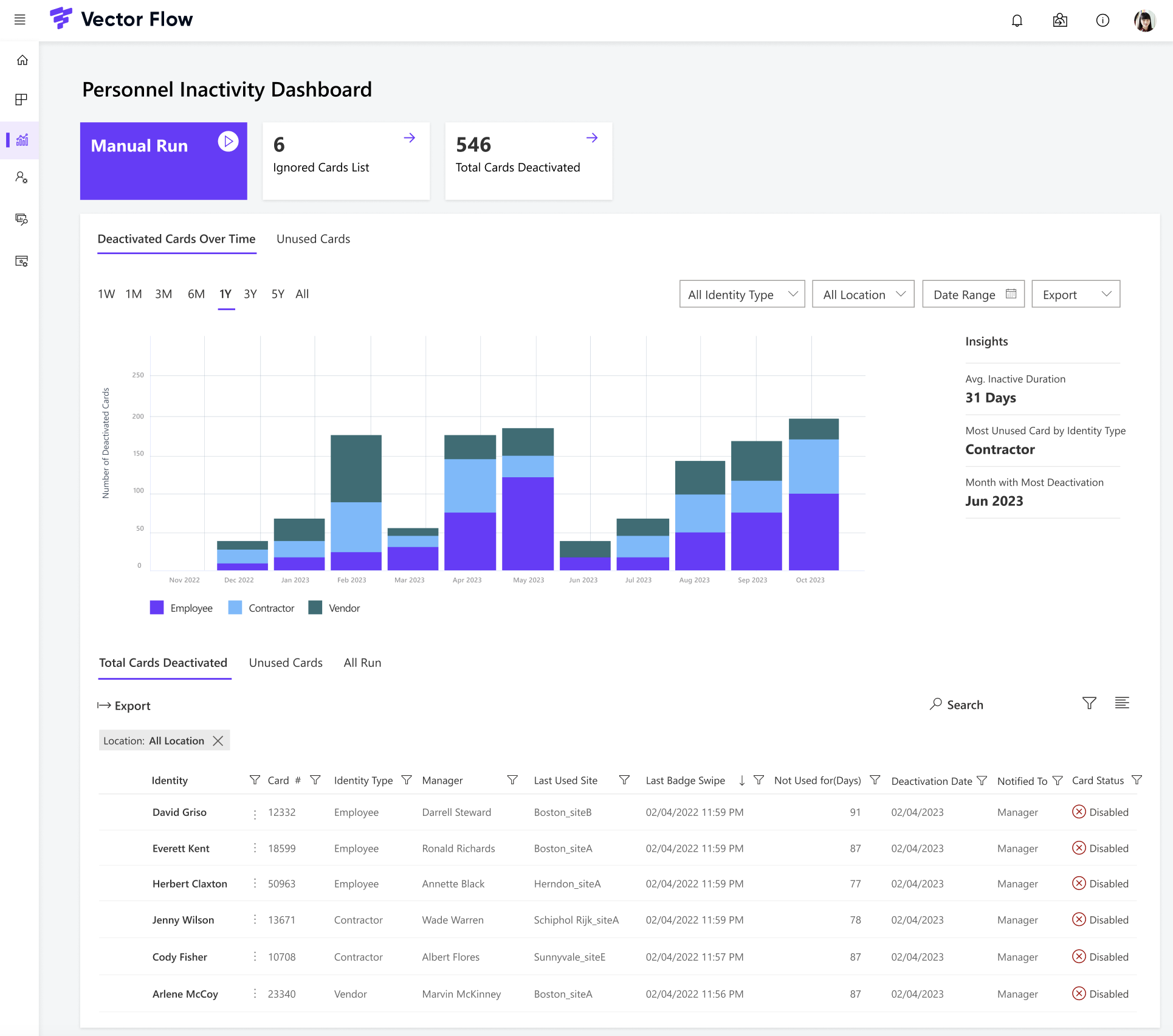
Proactive measures are the key to preventing security breaches. Vector Flow’s ‘Use it or Lose it’ Badge Audit feature takes security to the next level by proactively measuring all active access cards and automatically disabling unused cards for a predefined period for enhanced security.
Functions
- Automatically disables Physical Access Cards that are identified as unused for a predefined period
- This applies to all Active Cards, except those specific cards identified per “Exclusion” criteria
Business Impact
- Mitigates risk of potential insider threats or unauthorized access
- Deploys proactive security measures to identify and address potential security vulnerabilities
Smart Mustering App: Deploy Smart Mustering Processes and Policies with New Everbridge Integration
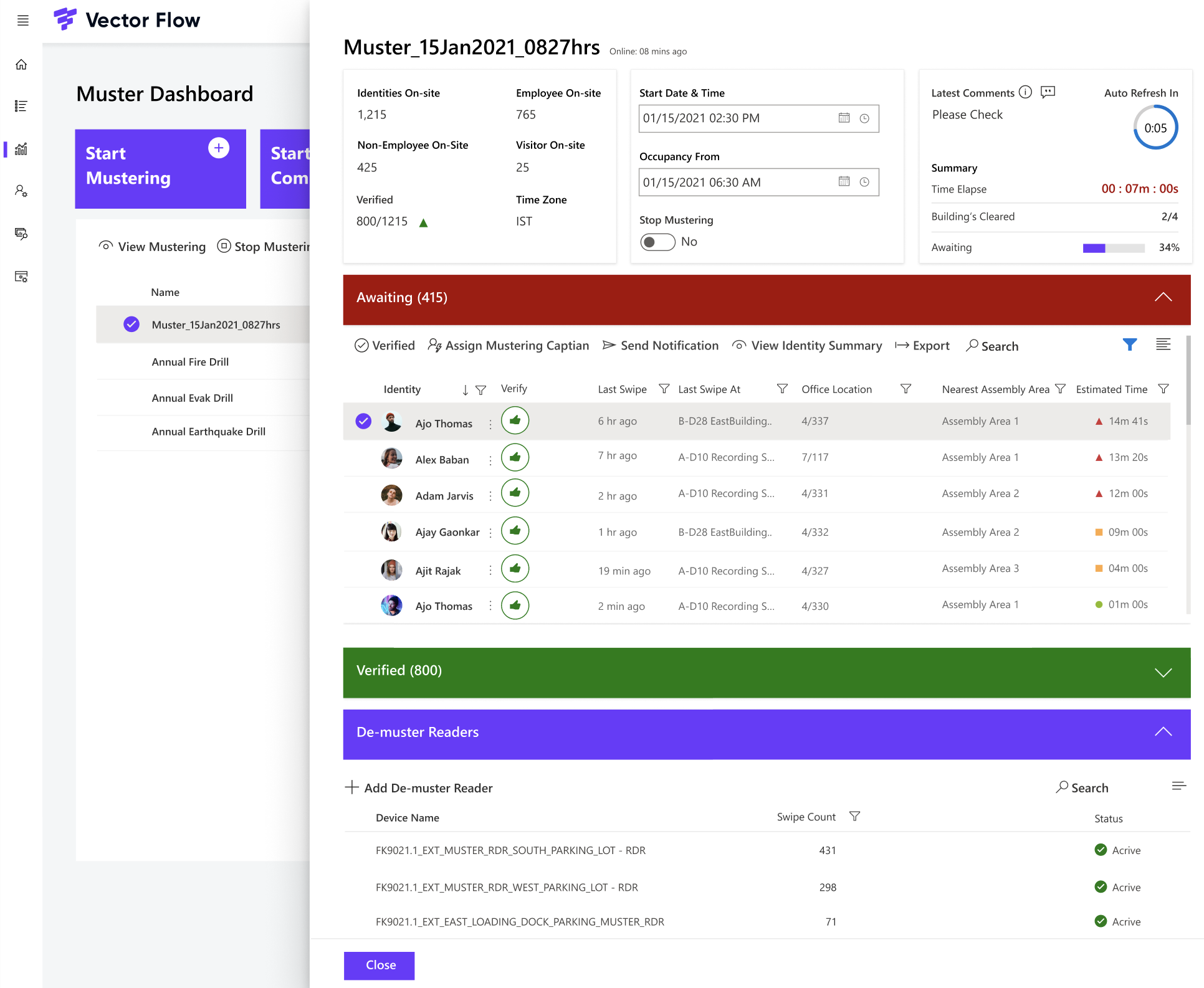
Emergency situations demand swift and efficient responses, especially when it comes to personnel evacuation. Our latest updates in the Smart Mustering App deliver a seamless and automated mustering process, minimizing chaos and confusion while also ensuring regulatory compliance related to emergency preparedness.
Functions
- Automates the mustering process by using card swipes to track personnel movement
- Provides real-time visibility into the mustering status of individuals including visitors, vendors, contractors, etc.
Business Impact
- Streamlines the evacuation process, minimizing chaos and confusion, and ensuring that everyone reaches the designated safe zones
- Ensures compliance requirements related to emergency preparedness and drills
PIAM App: New Service Level Agreement (SLA) Timers Improve Task Management
SLA timers play a crucial role in task management and accountability, helping to identify bottlenecks and improve internal communications. Vector Flow introduces new features within the Physical Identity and Access Management (PIAM) App to configure and personalize SLAs so that your team can better manage their tasks and stay compliant.
Functions
- Streamline task management processes by prioritizing and organizing tasks based on their urgency and importance
- Configuration streamlines workflows and processes by enabling users to automate tasks or set up rules that align with their organization
Business Impact
- SLA timers identify bottlenecks or delays in task/request completion
- SLA timers promote clear communication regarding task completion and response times
- Configurability provides flexibility to adapt to changing requirements
VIM App: Enhanced Watchlist and Training Now Integrated with Site Manager
The Vector Flow Visitor Identity Management (VIM) App updates introduce enhanced watchlists integrated with real-time updates and training, creating a comprehensive security ecosystem across all identities.
Functions
- Integrated watchlist allows to you screen entities/identities against various watchlist
- Automated training mandates ensure that only verified identities who have completed internal/external training are allowed to enter the site
- Provides real-time updates from authoritative sources (integrated business systems) and access to the latest information
Business Impact
- Automated watchlists ensure increased efficiency by reducing manual efforts, minimizing errors, and consistent screening
- Real-time screening results empower operators to make informed decisions promptly
- Integrated training ensures entities receive relevant training based on site/ location
- Reduce false positives in screening minimizes unnecessary disruptions
Our relentless dedication to simplifying security operations and enhancing efficiency is at the heart of everything we do at Vector Flow. With these updates, we aim to empower you with cutting-edge solutions that not only streamline risk management but also make your day just a little bit easier.
To schedule your own demo of a Vector Flow product or update, please contact us here
The Future of PIAM
The security industry has come a long way since the advent of PACS and legacy PIAM solutions. However, there is still much to be discovered in terms of data-automation as it relates to security. PIAM 2.0 sets new benchmarks in identity and visitor management, compliance, facility operations and occupancy management, emergency management and mustering, threat intelligence, SOC operations, and so much more. Such capabilities are already defining how companies are addressing digital transformation, so it becomes a more natural extension of those procedures and applications already in use today. PIAM 2.0 also underscores the growing imperative for enterprises to make use of data that is already available to them to facilitate higher levels of security, safety and efficiency. Imagine that this is just the beginning of PIAM 2.0. Contact us here to learn more.

